A week ago, I was in Tokyo waiting for a train. I had been staying in the crowded precinct of Shinjuku – a neon metropolis on the west side of the city. I bought a ticket for the Metro and was counting the seconds until midnight when the train would arrive to take me on my way. I was worried about my transfer; I knew that once I arrived at the station, I would have exactly seven minutes to sprint across the terminal, buy a ticket for the Keisei Rail, and hop on the next train.
I wondered why the process had to be so difficult. Why couldn’t the two railways integrate their ticketing systems so I could make a single purchase to travel the entire way? Wouldn’t that save everyone time and money? It’s ultimately just a question of user tracking. The two railways would need to record every touch point in the user’s journey in order to attribute share of credit to the appropriate organization. Does this sound familiar?
I’ve worked at Annalect for the past two-and-a-half years strategizing custom data and tracking solutions for brilliant clients like Levis, Activision, Mitsubishi, and Wells Fargo (among many others). As an ad technologist, I have watched the industry’s progression from standard desktop solutions, to mobile, and now to integrated cross-device technologies which promise to revolutionize the way we serve, track, and measure media impact.
In part 1 and part 2 of our mobile series, we spoke about building a mobile app that provides inherent value for your consumers. But once that is completed, you are faced with the task of driving your existing consumers to download and interact with that new app. Like any digital marketing effort, this will probably involve a wide mix of media channels, so the use of consistent, holistic user tracking will be essential for driving media optimization decisions. Unfortunately, due to basic limitations in mobile tracking, attributing app-downloads to media activity is exceptionally complex. Each of the mobile tracking methods currently available were created for specific types of serving environments, so they oftentimes do not function correctly when working cross-environment. A serving environment is defined as the specific browser or app in which tracking is taking place (Chrome is a separate serving environment from Safari which is a separate serving environment from in-app, etc..).
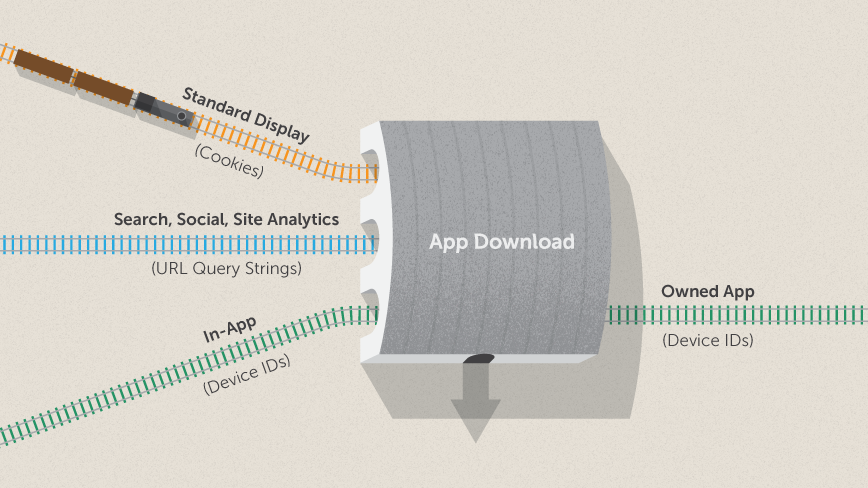
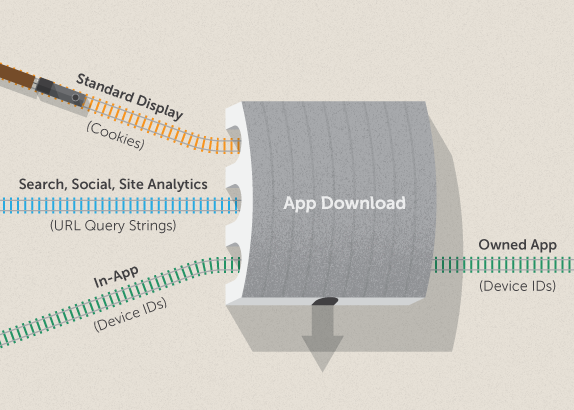
In the scenario above, the three railways each represent a grouping of mobile serving environments. Once a user navigates to the App Store and downloads your app, they are essentially “transferring” to a new environment (Owned App). The methodology used for in-app continues tracking through to conversion, but standard Display, Search, Social, and Site-Analytics tracking lose sight of the user.
All of the traditional tracking methodologies employed in mobile have cross-environment blind spots, so a holistic strategy for tracking app-downloads must consist of a combination of these methodologies, augmented by 1st or 2nd party data to facilitate the necessary cross-environment “transfers”.
Making the Transfer: Identity Management
Large enterprises can gather a vast amount of data about a user and their devices. These “user identity” connections can be formed cross-device and cross-environment, so they are capable of mitigating the limitations of traditional mobile tracking methodologies. This makes user identity management the most important data input for holistic app-download tracking.
There are two primary methods for determining user identity. If you trawl the internet on this topic, you will likely find that most material assesses the merits of deterministic vs. probabilistic tracking, but there are much easier (and less misleading) ways to explain this technology. So we will be going a different direction.
The two primary methods for determining cross-environment, or cross-device, user identity are Login Tracking and Device Fingerprinting.
Type 1: Login Tracking
Login Tracking methods utilize user-provided data (usually emails or login IDs) to directly identify single users across serving environments and platforms. This method relies on “opt-ins” from users who provide their personal information in exchange for a service. Login IDs may come from a technology firm’s 1st party data set (See: Facebook & Google), or your business’ own 1st party data (EX: A bank can make a cross-device connection if a user logs into their account from both their desktop and mobile app).
![]()
Before you board the first train, the conductor asks for your name. You happily provide it and step on the train. After transferring to the second railway, you are asked your name again.
The railways are able to identify you because you self-identified in both environments.
Data Quality: Login Tracking is the most reliable bridge for cross-device and cross-environment measurement because it utilizes connections that are directly verified by the users themselves. These connections provide a “panel” of users from whom the technology firm can extrapolate total attributed conversions (app-downloads) for the entire population.
Scalability: Due to complex limitations, users must log in to all available platform and serving environment combinations (Desktop Chrome, Mobile Safari, Mobile in-app, etc..) to allow login-based conversion tracking across those environments. Consequently, the feasibility of login tracking is directly related to the number of users who log in to your site properties. This limits small businesses and technology firms from developing this capability on their own due to their lower user volumes.
It is also important to note that login tracking is simply an augmentation to traditional mobile tracking (cookies and device IDs), so this method is ineffective when users are untrackable by traditional means (users blocking 3rd party cookies, or app environments where device IDs are not made available).
Type 2: Device Fingerprinting
“Device Fingerprinting” refers to tracking methodologies that collect unique (or semi-unique) hardware and network signals to statistically identify single users across serving environments and platforms. Some examples of common signals include Device Model, Operating System (OS) version, Mobile carrier, IP address, and preferred language. These signals are analyzed in the aggregate to determine the statistical probability that two actions were taken by the same user.
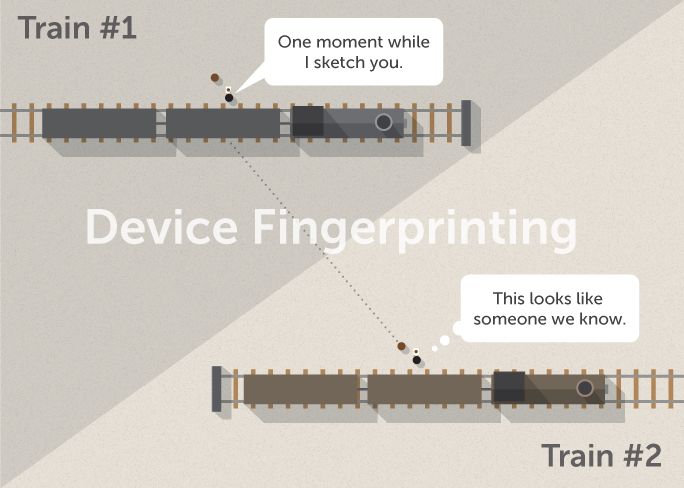
Before you board the first train, the conductor subtly sketches a rough picture of you. While boarding the second train, the conductor takes note of your approximate height, weight, and the color of your clothes.
The two railways are able to identify you by tying the descriptions gathered in the two environments.
Data Quality: Device Fingerprinting is an extremely reliable bridge for cross-environment measurement within a single device; this makes it an ideal solution for measuring media impact on app downloads. It is important to consider however, that fingerprinting is less adept at identifying cross-device connections since most of the recorded signals are device-specific (IP address being the main exception).
Scalability: These technologies can monitor and track any user, regardless of device or serving environment, without the need for explicit user consent. These firms’ scalability is only limited by the number of users that are being exposed to their technology within a given period (They cannot confidently identify a user’s device until they have seen them at least two or three times).
Identity Management is the Key
2016 is the year of Identity Management. It may be a daunting subject, but it is already shifting the paradigm of digital tracking and messaging closer to a 1:1 relationship between business and consumer. It has become the primary topic of conversation across a large number of use cases, so it is nearly impossible to talk about mobile technologies without eventually devolving into a conversation about identity data.
A mobile application can provide your business with a strong strategic advantage by bringing consumers closer to your brand and enhancing your consumers’ digital experience.
However, in order to reap these benefits, you must:
- Offer basic conveniences (rewards programs, discount incentives and easy transactions) for your consumer (part 1)
- Measure your ideas against both quantitative and qualitative data (part 2)
- Leverage identity management to holistically measure the source of your downloads to drive media optimization decisions (part 3)
Oh, and for those of you still in suspense, I made my connection, boarded my train, and arrived safely at home.